Stage setup
When using this stage with SharePoint Optimized V2 or LDAP ACLs V2 connectors, configure the following settings:| Field | Value |
|---|---|
| User ID source | query_param or header |
| User ID key | The key that contains the User ID |
Configure Security Trimming for SharePoint Optimized V2
Configure Security Trimming for SharePoint Optimized V2
Migrate older Fusion Graph Security Trimming stage setups to Fusion 5.9
Migrate older Fusion Graph Security Trimming stage setups to Fusion 5.9
This describes how to migrate your pre-Fusion 5.8 Graph Security Trimming query pipeline stage setup to Fusion 5.8 or later. It applies to deployments using:
- SharePoint Optimized V2 connector v1.1.0 or later
- LDAP ACLs V2 connector v1.4.0 or later to crawl Active Directory in Azure
- The LDAP ACLs V2 connector v1.2.0 or later to crawl Active Directory in LDAP
Migration
To migrate a deployment that is crawling Active Directory to Fusion 5.8 or later, follow these steps.Update the datasource configurations
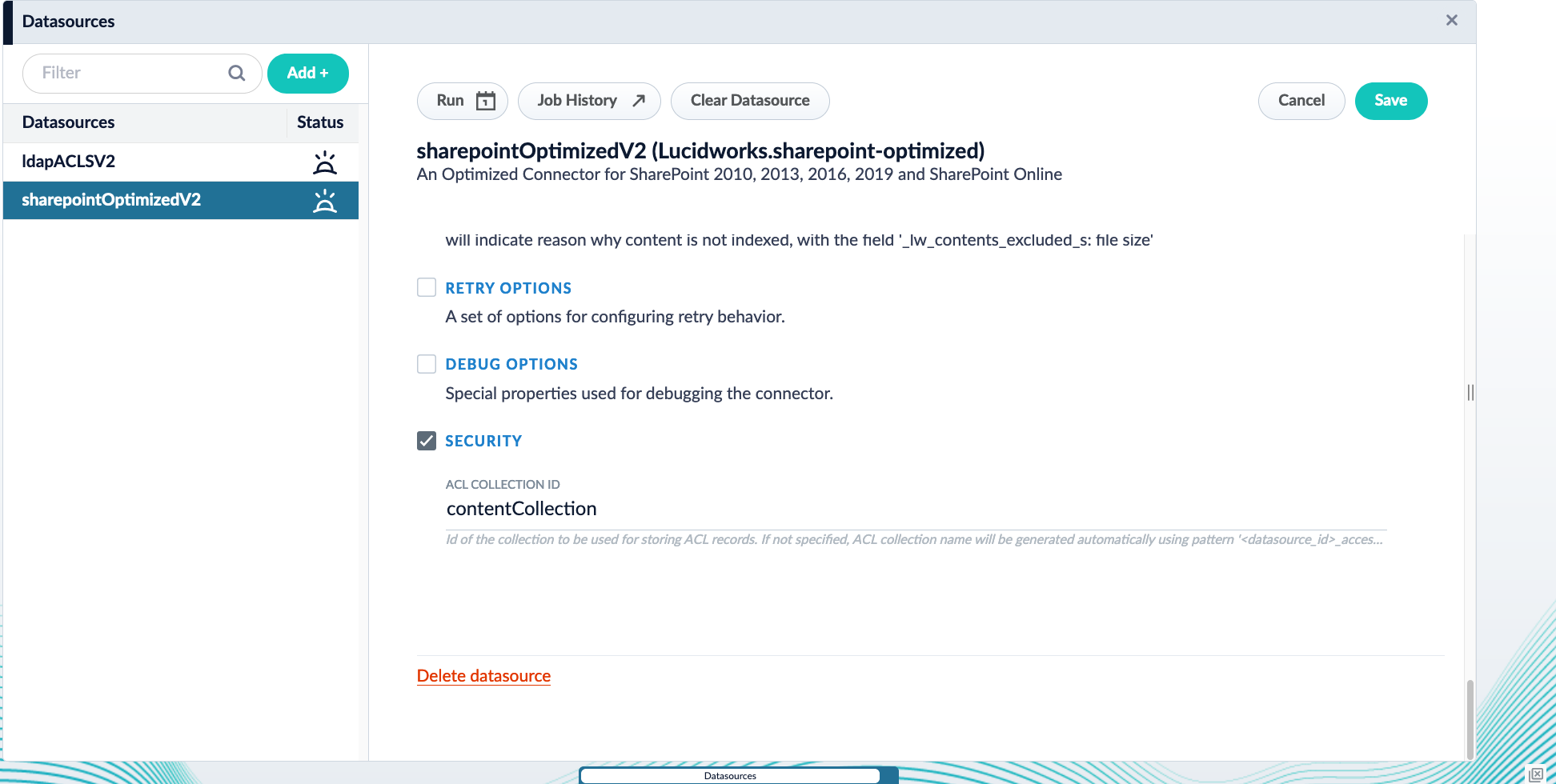
The SharePoint Optimized V2 and LDAP ACLs V2 datasources must index the content documents and ACL documents to the same collection. Ensure both datasources use the same value,contentCollection, for the field ACL Collection ID.If using SharePoint-Optimized and LDAP-ACLs < v2.0.0
Update the ACL Collection Id in the datasource configuration.The SharePoint-Optimized and LDAP-ACLs datasources must index theircontent_documents and acl_documents to the same collection. Make sure the property Security -> ACL Collection in both datasources have the same value. In both datasources, SharePoint-Optimized and LDAP-ACLs, check the property Security -> ACL Collection Id and make sure it points to the same content-collection.- Navigate to Indexing > Datasources.
- Open your SharePoint Optimized V2 or LDAP ACLs V2 datasource.
- Under Security, update the configuration to use
contentCollectionas the ACL Collection ID. The Security checkbox must be checked for this field to appear. - Save the configuration.
If using SharePoint-Optimized and LDAP-ACLs >= v2.0.0
Recreate or update the datasources. If only updated, it is not possible to go back to the configuration of a previous plugin version.By default, the LDAP-ACLs and SharePoint-Optimized V2 datasources will index thecontent_documents and acl_documents to the same collection.- Navigate to Indexing > Datasources.
- Open your SharePoint Optimized V2 or LDAP ACLs V2 datasource.
- Under Graph Security Filtering Configuration, select Enable security trimming.
Clear the datasources and perform a full crawl
- Navigate to Indexing > Datasources.
- Open your SharePoint Optimized V2 or LDAP ACLs V2 datasource.
- Click the Clear Datasource button, and choose yes.
- Navigate to Collections > Collections Manager.
- Verify that the
job_statecollection is empty. - Return to your datasource.
- Click Run > Start to reindex your data.
Configuring Graph Security Trimming
The quick learning for Configuring Graph Security Trimming focuses on how to set up security trimming.