Secret definition
Config Sync doesn’t have a specific secret concept. Secrets are defined as part of the Fusion configuration files. Fusion usesdefault@encoded-secret as the secret value in the configuration files and ConfigSync rely on this value to manage secrets.
Options
Config Sync supports the following options for managing secrets:- Keep secrets decoded in the repository.
- Keep secrets encoded in the repository and the actual secret stored in a Kubernetes secret.
Keep secrets decoded in the repository
In this approach, the actual secret is stored in the repository in plain text.Pros
- Easy to manage.
- No need to manage multiple secrets.
Cons
- Security risk.
- Anyone with access to the repository can manage the secret.
Keep secrets encoded in the repository and the actual secret stored in a Kubernetes secret
In this approach, the actual secret is stored in a Kubernetes secret and the encoded secret is stored in the repository. Encoded secret value is the same as in Fusion:xXx-Redacted-xXx.
Config Sync matches the encoded secret in the repository with the actual secret in the Kubernetes secret using the secret data and labels:
- labels:
app.kubernetes.io/part-of=config-sync- data:
file: The file name of the file in the repository (such asapp/datasources-v2/ds-name.json)path: JSON pointer to the secret in the file (such as/properties/password)value: The encoded secret value
Syncing secrets (encoded secret) between Fusion and Kubernetes secret
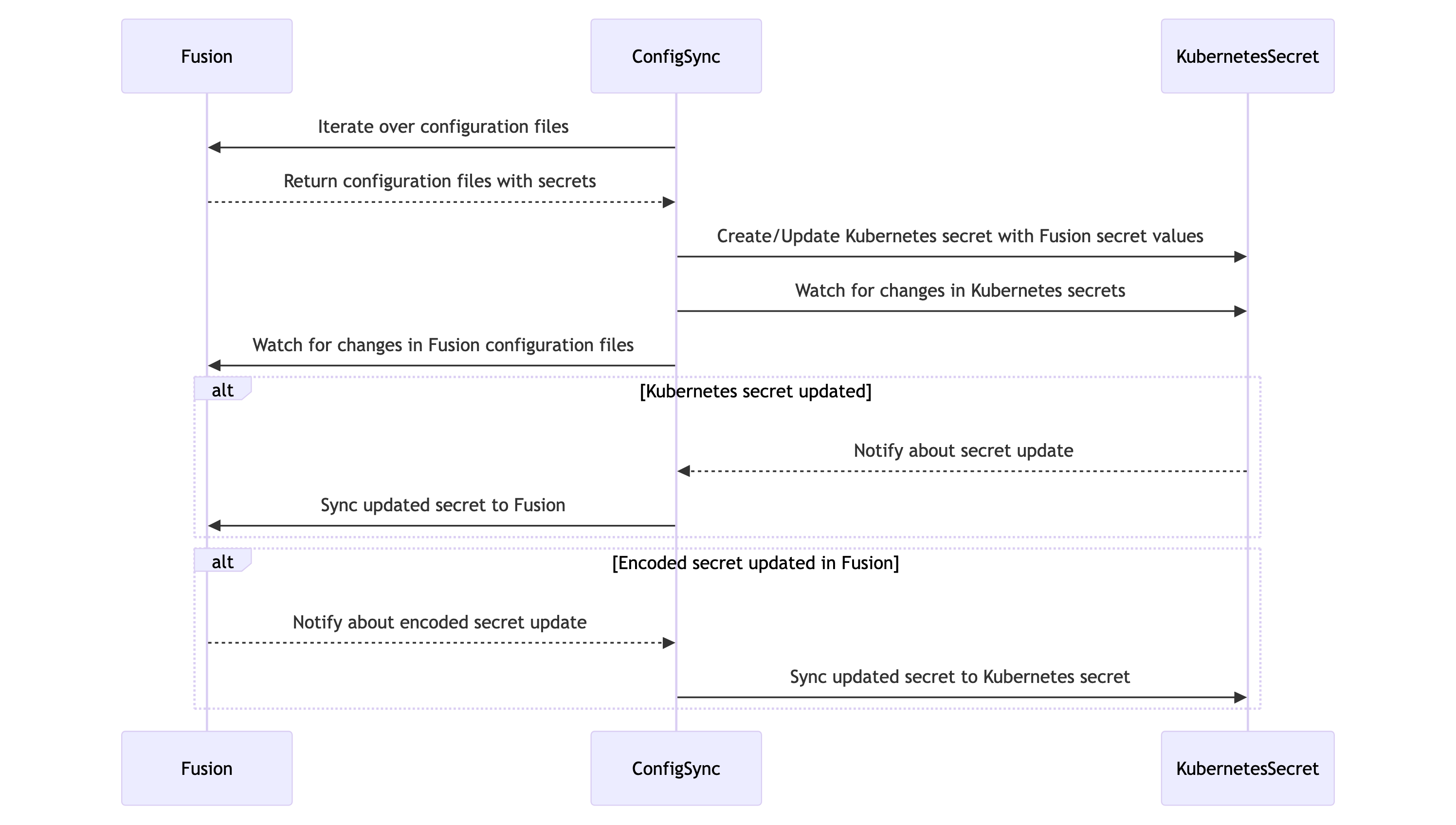
Config Sync supports both way sync for secrets. It can sync the actual secret from the Kubernetes secret to Fusion and vice versa.Initial sync
When Config Sync is started, it iterates over all the Fusion configuration files and check if there is any secret in the configuration file. For each secret, it creates or updates the Kubernetes secret with the encoded secret value. After that, it starts watching the Kubernetes secrets and any changes in the Kubernetes secret is synced to Fusion.Syncing from Kubernetes secret to Fusion
If the actual secret is updated in the Kubernetes secret, Config Sync syncs the updated secret to Fusion. It’s important that Config Sync is up and running to sync the updated secret to Fusion.Syncing from Fusion to Kubernetes secret
If the encoded secret is updated in the Fusion, Config Sync syncs the updated secret to the Kubernetes secret.