- Authenticating UI users – Fusion authenticates users when they log in. Logging in creates a new Fusion session. Fusion also authenticates users when the Sessions REST API creates a session.
-
Authorizing UI users – Fusion authorizes users to use specific parts of the Fusion UI.
UI users must also be authorized to make API requests, because the UI makes API requests.
- Authenticating and authorizing users who make API requests
- Password Encryption- Fusion uses 128-bit AES keys to encrypt passwords and “AES/CBC/PKCS7Padding” for the cipher. The ciphertext is also signed.
- Using session cookies
- Using an external authentication provider (optional) - A security realm can specify use of an external authentication provider, such as LDAP, JWT, or SAML.
- Using SSL/TLS to ensure that data in flight between your application and Fusion is not observable (optional) - See SSL Security (Unix) or SSL Security (Windows). For more information, see Transport Layer Security.
- Constraining the documents that are indexed (optional)
- Trimming the documents that are returned by queries based on authorization (optional)
SSL Security (Unix)
SSL Security (Unix)
Fusion’s UI (which is accessed through the Fusion Proxy service) can run over SSL for secure communication with any HTTP client, using the
Java Secure Socket Extension (JSSE) framework. You configure Fusion for SSL by configuring Fusion’s Proxy and UI services.If Fusion is behind a firewall, you can use a self-signed certificate for SSL communication with other hosts in your internal network. Create a keystore for the Fusion Proxy service and load the keystore with the self-signed PKCS #12 certificate.To store certificates, you can use the Java keytool
Key and Certificate Management utility which is a part of the JDK.How to create a keystore and load a self-signed certificateWhere In a production environment, SSL certificates typically originate with certificate signing requests (CSRs) and are signed by a trusted third-party Certificate Authority (CA).The steps here assume that you are the person who will be obtaining the SSL certificate chain and private key files. If you are not that person, contact your system administrator.With the certificate chain and private key as separate files, use the You can only use this alternative if your SSL certificate covers a hostname that can be accessed from the local host. For example, if your certificate only covers
Fusion 4.0.2 or later is required to enable SSL security. Version 4.0.2 fixed a bug in the authentication proxy that incorrectly redirected some requests when SSL is enabled.
Required software
Configuring Fusion for SSL requires the following software:- Java Development Kit. To store certificates, you can use the Java keytool Key and Certificate Management utility which is a part of the JDK. The JDK is also a requirement for Fusion Server.
-
OpenSSL. You might need the
opensslcommand line tool:- If you have the certificate chain and private key as separate files, then you can use the
opensslcommand line tool to create a PKCS #12 file. - If you have an intermediate CA certificate, then you can use it and
opensslto generate the certificate chain and private key files.
- If you have the certificate chain and private key as separate files, then you can use the
Load an SSL certificate into a Fusion keystore
The SSL protocol is based on public-key cryptography where encryption keys come in public key/private key pairs. An SSL certificate is used to verify the authenticity of a particular server. It contains the web site name, contact email address, company information and the public key used to encrypt the communication which is shared with the entities that communicate with the owner of the public/private key pair.The server has a locally-protected private key that is accessible using a JSEE keystore.The keystore maintains both the server certificate and the private key, so that when a server authenticates itself to the client, it uses the private key from its keystore for the initial SSL handshake.Load the certificate into a Fusion keystore. Perform the tasks in the appropriate section:- Self-signed certificate. If Fusion is behind a firewall, you can use a self-signed certificate for SSL communication with other hosts in your internal network. Create a keystore for the Fusion Proxy service and load the keystore with the self-signed PKCS #12 certificate.
- Certificate signed by a certificate authority. In a production environment, SSL certificates typically originate with certificate signing requests (CSRs) and are signed by a trusted third-party Certificate Authority (CA). Create a keystore for the Fusion Proxy service and load the keystore with the PKCS #12 certificate from a CA.
Alternative 1: Self-signed certificate
If you are using a CSR-originated certificate from a trusted certificate authority, proceed to Alternative 2: CA-signed certificate.
-
Set environment variables:
For example, in Fusion 4.1:In Fusion 4.0.x:
-
Create the Fusion Proxy service keystore, generate the key pair and self-signed certificate, and load them into the keystore:
Example command:You must include the qualified domain name and/or the IP address of the Fusion server in the
-ext SANpart of the command. Failure to do so results in SSL validation errors.
ProxyPort is the Fusion Proxy port.Alternative 2: CA-signed certificate
If Fusion is behind a firewall and you are using a self-signed certificate, skip this section. Perform the tasks in Alternative 1: Self-signed certificate.
Preliminary steps
- Obtain a domain from a domain registrar.
- Change the A record of your domain to the public IP address of your web server instance.
Generate SSL certificate files
Use an SSL certificate provider to generate the certificate chain and private key files, or a PKCS #12 certificate, from a trusted CA:- Certificate chain and private key files. In this case, you will need to convert these files into a single certificate file in PKCS #12 format.
- A PKCS #12 certificate. This must contain both the certificate chain and private key. In this case, no conversion is necessary.
- In most cases, you will need to temporarily open ports 80 and 443 in your firewall configuration. The SSL certificate provider must be able to make successful HTTP and HTTPS requests to your server through the Domain Name System (DNS).
- Use an SSL certificate provider to generate the certificate chain (
fullchain.pem) and private key (privkey.pem) files, or the PKCS #12 certificate, from a trusted CA. Steps will vary based on the certificate provider. Contact your certificate provider for details. - Close ports 80 and 443 in your firewall configuration.
- Change the A record of your domain to the public domain-name address of your web server instance.
- If you have certificate chain and private key files, perform the steps in Convert the certificate chain and private key files to a PKCS #12 certificate and Import the PKCS #12 certificate into the Fusion Proxy service keystore.
- If you have a PKCS #12 certificate, perform the steps in Import the PKCS #12 certificate into the Fusion Proxy service keystore.
Convert the certificate chain and private key files to a PKCS #12 certificate
If you have a PKCS #12 certificate, skip this section and proceed to the section Import the PKCS #12 certificate into the Fusion Proxy service keystore.
openssl command line tool in OpenSSL to create a PKCS #12 certificate.Do not enter a blank password.
Create the Fusion Proxy service keystore and import the PKCS #12 certificate
Use the Java keytool Key and Certificate Management utility to create a keystore for the Fusion Proxy service ($FUSION_HOME/apps/jetty/proxy/etc/keystore) and import the PKCS #12 certificate file. Fusion uses this certificate to perform SSL.- To create the keystore and import the PKCS #12 certificate:
-
Use the keytool
importcommand to create a JSSE keystore. -
(Optional) If desired, delete the PKCS #12 certificate file that resides outside of the Fusion Proxy service keystore (the one you created from the certificate chain and private key files, or obtained from a trusted CA.
Enable HTTPS in the Fusion Proxy service
Before beginning these steps, load an SSL certificate into a Fusion keystore.How to enable HTTPS in the Fusion Proxy service:-
(Only for Fusion Server 4.0.x and 4.1.0) Prevent the
start.jarprogram from downloading a default keystore file, which is not needed. Edit$FUSION_HOME/apps/jetty/home/modules/ssl.mod. Comment out the indicated line using#. Change:To: -
Set environment variables:
For example, in Fusion 4.1:In Fusion 4.0:
-
Add HTTPS protocol support to the Jetty TLS (SSL) connector:
Example output:
-
Get the obfuscated version of your keystore password:
Replace
PASSWORDwith the password you used for the keystore. If the password contains special characters, URL encode them. Example output: -
Edit the file
$FUSION_HOME/apps/jetty/proxy/start.ini:-
Include obfuscated passwords by adding these properties to the end of the file:
-
Use the OBF-encrypted password from step 4 (including the
OBF:string) as the value for all three of the properties.
For example: -
Set the local SSL port by adding the
jetty.ssl.portproperty to the end of the file, and providing the port number. For example: -
Save the file
$FUSION_HOME/apps/jetty/proxy/start.ini.
-
Include obfuscated passwords by adding these properties to the end of the file:
Restart Fusion and test access through HTTPS
-
Restart all Fusion services:
HTTPS should now be enabled in the Fusion Proxy service.
-
Sign in to the Fusion UI. Specify the HTTPS URL scheme and SSL port, for example,
https://search.mycorp:8443.
Disable HTTP access to the Fusion Proxy service
Disable HTTP access. You have a choice. Perform the tasks in the appropriate section:- Disable HTTP access on the firewall or load balancer - This is the preferred approach.
- Disable listening for HTTP requests in the Fusion Proxy service
Alternative 1: Disable HTTP access on the firewall or load balancer
Disable HTTP access to the Fusion Proxy service on the firewall or load balancer:- Disallow all requests for port 8764 from the outside world. Only
localhostshould be able to communicate with Fusion on the non-SSL port 8764. Block all other requestors. - If you are using a firewall or load balancer in front of Fusion, use it to redirect all HTTP requests to use HTTPS instead. For example, Apache would redirect all incoming HTTP traffic to HTTPS.
Alternative 2: Disable listening for HTTP requests in the Fusion Proxy service
Ideally, you should disable HTTP access using the firewall or load balancer. Follow the steps in this section only if disabling HTTP access on the firewall or load balancer is not feasible.
https://fusion.com, then your local machine must be able to access Fusion from that exact host. If necessary, change the hosts file so that this can work.How to disable HTTP- Edit
/opt/lucidworks/fusion/latest.x/apps/jetty/proxy/start.d/http.ini.-
Change this line:
To:
- Save the file.
-
Change this line:
- Edit the Fusion configuration file,
/opt/lucidworks/fusion/latest.x/conf/fusion.cors(fusion.propertiesin Fusion 4.x).-
Ensure that the Agent JVM uses the Fusion Proxy service’s keystore by adding this to the end of the file:
Replace
PASSWORDwith your Fusion keystore password. -
Uncomment the
default.addressand change it to the hostname of the server that is validated by your SSL certificate.
If the hostname saved indefault.addressis not validated by your SSL certificate, then the Fusion Proxy service will not start, because the agent’s liveness detector will not be able to access the HTTPS port to determine whether Fusion is running.For example, if your SSL certificate’s validated hostname isIf you self-signed the certificate, then thedefault.addressmust match the hostname you specified while signing the certificate. Failure to do this will result in the Fusion Proxy service not starting after you have disabled HTTP.search.mycorp, then change:To: -
Change the
proxy.portto the SSL port you chose. -
Uncomment
proxy.ssland change its value totrue. Change:To:
-
Ensure that the Agent JVM uses the Fusion Proxy service’s keystore by adding this to the end of the file:
References and tutorials
- Transport Layer Security (Wikipedia)
- Public Key Certificate (Wikipedia)
- OpenSSL Cookbook (free ebook)
- OpenSSL Command Line Utilities (OpenSSL wiki)
- Java Tutorials: Generating and Verifying Certificates
- IBM developerWorks: What is the JSSE all about?
SSL Security (Windows)
SSL Security (Windows)
Fusion’s UI (which is accessed through the Fusion Proxy service) can run over SSL for secure communication with any HTTP client, using the
Java Secure Socket Extension (JSSE) framework. You configure Fusion for SSL by configuring Fusion’s Proxy and UI services.If Fusion is behind a firewall, you can use a self-signed certificate for SSL communication with other hosts in your internal network. Create a keystore for the Fusion Proxy service and load the keystore with the self-signed PKCS #12 certificate.To store certificates, you can use the Java keytool
Key and Certificate Management utility which is a part of the JDK.How to create a keystore and load a self-signed certificateWhere In a production environment, SSL certificates typically originate with certificate signing requests (CSRs) and are signed by a trusted third-party Certificate Authority (CA).The steps here assume that you are the person who will be obtaining the SSL certificate chain and private key files. If you are not that person, contact your system administrator.How to create a PKCS #12 certificateWith the certificate chain and private key as separate files, use the You can only use this alternative if your SSL certificate covers a hostname that can be accessed from the local host. For example, if your certificate only covers
Fusion 4.0.2 or later is required to enable SSL security. Version 4.0.2 fixed a bug in the authentication proxy that incorrectly redirected some requests when SSL is enabled.
Required software
Configuring Fusion for SSL requires the following software:- Java Development Kit. To store certificates, you can use the Java keytool Key and Certificate Management utility which is a part of the JDK. The JDK is also a requirement for Fusion Server.
-
OpenSSL. You might need the
opensslcommand line tool:- If you have the certificate chain and private key as separate files, then you can use the
opensslcommand line tool to create a PKCS #12 file. - If you have an intermediate CA certificate, then you can use it and
opensslto generate the certificate chain and private key files.
- If you have the certificate chain and private key as separate files, then you can use the
Overview of procedure
How to configure Fusion for SSL:- Load an SSL certificate into a Fusion keystore.
- Enable SSL in the Fusion Proxy service.
- Restart Fusion and test access through HTTPS.
- Disable HTTP access to the Fusion Proxy service.
Load an SSL certificate into a Fusion keystore
The SSL protocol is based on public-key cryptography where encryption keys come in public key/private key pairs. An SSL certificate is used to verify the authenticity of a particular server. It contains the web site name, contact email address, company information and the public key used to encrypt the communication which is shared with the entities that communicate with the owner of the public/private key pair.The server has a locally-protected private key that is accessible using a JSEE keystore.The keystore maintains both the server certificate and the private key, so that when a server authenticates itself to the client, it uses the private key from its keystore for the initial SSL handshake.Load the certificate into a Fusion keystore. Perform the tasks in the appropriate section:- Self-signed certificate. If Fusion is behind a firewall, you can use a self-signed certificate for SSL communication with other hosts in your internal network. Create a keystore for the Fusion Proxy service and load the keystore with the self-signed PKCS #12 certificate.
- Certificate signed by a certificate authority. In a production environment, SSL certificates typically originate with certificate signing requests (CSRs) and are signed by a trusted third-party Certificate Authority (CA). Create a keystore for the Fusion Proxy service and load the keystore with the PKCS #12 certificate from a CA.
Alternative 1: Self-signed certificate
If you are using a CSR-originated certificate from a trusted certificate authority, proceed to Alternative 2: CA-signed certificate.
-
Set environment variables:
-
Create the Fusion Proxy service keystore, generate the key pair and self-signed certificate, and load them into the keystore:
Example command:You must include the qualified domain name and/or the IP address of the Fusion server in the
-ext SANpart of the command. Failure to do so results in SSL validation errors.The resulting certificate enables validated SSL transport to these hosts:
ProxyPort is the Fusion Proxy port.Alternative 2: CA-signed certificate
If Fusion is behind a firewall and you are using a self-signed certificate, skip this section. Perform the tasks in Alternative 1: Self-signed certificate.
Preliminary steps
- Obtain a domain from a domain registrar.
- Change the A record of your domain to the public IP address of your web server instance.
Generate SSL certificate files
Use an SSL certificate provider to generate the certificate chain and private key files, or a PKCS #12 certificate, from a trusted CA:- Certificate chain and private key files. In this case, you will need to convert these files into a single certificate file in PKCS #12 format.
- A PKCS #12 certificate that contains both the certificate chain and private key. In this case, no conversion is necessary.
- In most cases, you will need to temporarily open ports 80 and 443 in your firewall configuration. The SSL certificate provider must be able to make successful HTTP and HTTPS requests to your server through the Domain Name System (DNS).
- Use an SSL certificate provider to generate the certificate chain (
fullchain.pem) and private key (privkey.pem) files, or the PKCS #12 certificate, from a trusted CA. Steps will vary based on the certificate provider. Contact your certificate provider for details. - Close ports 80 and 443 in your firewall configuration.
- Change the A record of your domain to the public domain-name address of your web server instance.
- If you have certificate chain and private key files, perform the steps in Convert the certificate chain and private key files to a PKCS #12 certificate and Import the PKCS #12 certificate into the Fusion Proxy service keystore.
- If you have a PKCS #12 certificate, perform the steps in Import the PKCS #12 certificate into the Fusion Proxy service keystore.
Convert the certificate chain and private key files to a PKCS #12 certificate
If you have a PKCS #12 certificate, skip this section and proceed to the section Import the PKCS #12 certificate into the Fusion Proxy service keystore.
openssl command line tool in OpenSSL to create a PKCS #12 certificate.Do not enter a blank password.
Create the Fusion Proxy service keystore and import the PKCS #12 certificate
Use the Java keytool Key and Certificate Management utility to create a keystore for the Fusion Proxy service (%FUSION_HOME%\apps\jetty\proxy\etc\keystore) and import the PKCS #12 certificate file. Fusion uses this certificate to perform SSL.If you are starting with a certificate file in PFX format (file extension
.pfx), that format is now identical to PKCS #12 format.-
To create the keystore and import the PKCS #12 certificate:
-
Use the keytool
importcommand to create a JSSE keystore. -
(Optional) If desired, delete the PKCS #12 certificate file that resides outside of the Fusion Proxy service keystore (the one you created from the certificate chain and private key files, or obtained from a trusted CA.
Enable HTTPS in the Fusion Proxy service
Before beginning these steps, load an SSL certificate into a Fusion keystore.How to enable HTTPS in the Fusion Proxy service:-
Set environment variables:
-
Add HTTPS protocol support to the Jetty TLS (SSL) connector:
Example output:
-
Get the obfuscated version of your keystore password:
Replace
PASSWORDwith the password you used for the keystore. If the password contains special characters, URL encode them. Example output: -
Edit the file
%FUSION_HOME%\apps\jetty\proxy\start.ini:-
Include obfuscated passwords by adding these properties to the end of the file:
jetty.sslContext.keyStorePasswordjetty.sslContext.keyManagerPasswordjetty.sslContext.trustStorePassword
-
Use the OBF-encrypted password from step 4 (including the
OBF:string) as the value for all three of the properties.
For example: -
Set the local SSL port by adding the
jetty.ssl.portproperty to the end of the file, and providing the port number. For example: -
Save the file
%FUSION_HOME%\apps\jetty\proxy\start.ini.
-
Include obfuscated passwords by adding these properties to the end of the file:
Restart Fusion and test access through HTTPS
-
Restart all Fusion services:
HTTPS should now be enabled in the Fusion Proxy service.
-
Sign in to the Fusion UI. Specify the HTTPS URL scheme and SSL port, for example,
https://search.mycorp:8443.
Disable HTTP access to the Fusion Proxy service
Disable HTTP access. You have a choice. Perform the tasks in the appropriate section:- Disable HTTP access on the firewall or load balancer - This is the preferred approach.
- Disable listening for HTTP requests in the Fusion Proxy service
Alternative 1: Disable HTTP access on the firewall or load balancer
Disable HTTP access to the Fusion Proxy service on the firewall or load balancer:- Disallow all requests for port 8764 from the outside world. Only
localhostshould be able to communicate with Fusion on the non-SSL port 8764. Block all other requestors. - If you are using a firewall or load balancer in front of Fusion, use it to redirect all HTTP requests to use HTTPS instead. For example, Apache would redirect all incoming HTTP traffic to HTTPS.
Alternative 2: Disable listening for HTTP requests in the Fusion Proxy service
Ideally, you should disable HTTP access using the firewall or load balancer. Follow the steps in this section only if disabling HTTP access on the firewall or load balancer is not feasible.
https://fusion.com, then your local machine must be able to access Fusion from that exact host. If necessary, change the hosts file so that this can work.How to disable HTTP- Edit
\lucidworks\fusion{backslash}latest.x\apps\jetty\proxy\start.d\http.ini.-
Change this line:
To:
- Save the file.
-
Change this line:
- Edit the Fusion configuration file,
\lucidworks\fusion{backslash}latest.x\conf\fusion.cors(fusion.propertiesin Fusion 4.x).-
Ensure that the Agent JVM uses the Fusion Proxy service’s keystore by adding this to the end of the file:
Replace
PASSWORDwith your Fusion keystore password. -
Uncomment the
default.addressand change it to the hostname of the server that is validated by your SSL certificate.
If the hostname saved indefault.addressis not validated by your SSL certificate, then the Fusion Proxy service will not start, because the agent’s liveness detector will not be able to access the HTTPS port to determine whether Fusion is running.For example, if your SSL certificate’s validated hostname isIf you self-signed the certificate, then thedefault.addressmust match the hostname you specified while signing the certificate. Failure to do this will result in the Fusion Proxy service not starting after you have disabled HTTP.search.mycorp, then change:To: -
Change the
proxy.portto the SSL port you chose. For example, change:To: -
Uncomment
proxy.ssland change its value totrue. Change:To:
-
Ensure that the Agent JVM uses the Fusion Proxy service’s keystore by adding this to the end of the file:
References and tutorials
- Transport Layer Security (Wikipedia)
- Public Key Certificate (Wikipedia)
- OpenSSL Cookbook (free ebook)
- OpenSSL Command Line Utilities (OpenSSL wiki)
- Java Tutorials: Generating and Verifying Certificates
- IBM developerWorks: What is the JSSE all about?
Fusion user login
When logging into the Fusion UI, a user provides a username and password, as well as their assigned security realm. An administrator must specify these in Fusion (using the native security realm) or configure Fusion to use an external authentication provider (for example, LDAP or SAML). See Access control. Fusion uses roles defined by permissions to authorize Fusion UI access and perform tasks in Fusion, including searching. The recommended method to delegate permissions is as follows:- Assign each user to a role and create custom roles as needed.
- Assign permissions on a per-app basis.
Manage users with security realms
Fusion uses security realms to authenticate users of the Fusion UI. Each user has an assigned security realm, which the user must select when logging in. If the user selects a different realm, authentication fails. A security realm also provides a list of roles as follows:- The list always includes the role(s) that are specified in the security realm.
- (Optional) If an external directory service (such as LDAP) is used for authentication, the list can also contain roles that are mapped from the names of the directory-service groups. That is, you can configure a security realm to return group information for users from that same directory service.
- (Optional) The security realm can reference one or more Fusion roles or, when using an external directory service provider, use group membership information from the provider to determine roles for users. Fusion maps the group names to role names and adds these roles to the user’s list of roles.
Fusion does not use permissions from LDAP to authorize UI access or API requests. It only obtains group names (optionally), which are used as role names or are mapped to role names. If an Active Directory Security Query Trimming Stage is used, then directory-service permissions are used for trimming. If a connector supports security trimming, then connector permissions are used for trimming.
Per-request authentication
Requests to the Fusion REST API must specify a security realm for per-request authentication, unless a session cookie is used (which contains information about the security realm). Fusion authorizes requested operations based on API permissions specified for the user and for the user’s role(s). Fusion considers the role(s) specified in the user definition and in the security realm. Fusion creates a list of roles when a session is created, that is, when a user logs in or when the Sessions REST API creates a session. Authorization based on permissions and its layering is at request time. You can define multiple security realms for a Fusion instance. A Fusion instance can manage multiple security realms, which allows users from different domains to have (different levels of) access to specific Fusion collections.Read-only root file system
Fusion 5.9.9 and later supports a read-only root file system to safeguard against unauthorized modifications, protecting your deployment against malicious software and other attacks. Most services operate efficiently in this mode, and for components that need write access, a separate writable mount is available using specific helm configurations. Read-only mode should only be enabled for services that do not require CRUD access. See Enable Read-Only Root File System for examples of how to configure this feature.Enable Read-Only Root File System
Enable Read-Only Root File System
This topic describes how to configure a read-only root file system for a Fusion deployment.
Read-only mode safeguards your file system against unauthorized changes, such as by malicious software or other attacks.
Enabling this feature entails configuring the Beginning with Fusion 5.9.10, all of Fusion’s services are designed to work with a read-only root file system, but some external services may require write access to the file system.
In that case, you can configure a read-only root file system and mount a separate writable file system for these services.The examples below show how to configure a read-only root file system for various Fusion services.With optional services:With optional services:With optional services:
readOnlyRootFilesystem attribute in the Fusion Helm chart.This feature is available starting in Fusion 5.9.9 and in all subsequent Fusion 5.9 releases.
Solr
Zookeeper
Kafka
ML Model Service
Argo
Seldon Core Operator
Argo Common Workflows
Question Answering
Classification
All-in-one values.yaml example
All-in-one values.yaml with optional services example
Supported services
The table below lists the services that support a read-only root file system, the ones that have it enabled by default, and the Fusion release in which support was added:| Chart Name | Pod Name | Container Name | Supported | Default enabled | Supported version |
|---|---|---|---|---|---|
| admin-ui | admin-ui | admin-ui | ✅ | ✅ | 5.9.9+ |
| api-gateway | api-gateway | init/api-gateway | ✅ | ✅ | 5.9.9+ |
| api-gateway | api-gateway | api-gateway | ✅ | ✅ | 5.9.9+ |
| api-gateway | api-gateway | generate-jks | ✅ | ✅ | 5.9.9+ |
| apps-manager | apps-manager | apps-manager | ✅ | ✅ | 5.9.9+ |
| argo | argo-server | argo-server | ✅ | ❌ | 5.9.10+ |
| argo | argo-executor | executor | ✅ | ❌ | 5.9.10+ |
| argo | argo-mainContainer | mainContainer | ✅ | ❌ | 5.9.10+ |
| argo | argo-controller | controller | ✅ | ✅ | 5.9.10+ |
| argo/minio | minio | minio | ✅ | ❌ | 5.9.10+ |
| argo/minio | minio | minio | ✅ | ❌ | 5.9.10+ |
| argo/minio | make-bucket-job | minio-mc | ✅ | ❌ | 5.9.10+ |
| argo-common-workflows | delete-model | init/main/wait | ✅ | ❌ | 5.9.10+ |
| argo-common-workflows | deploy-model | init/main/wait | ✅ | ❌ | 5.9.10+ |
| argo-common-workflows | milvus-maintenance | init/main/wait | ✅ | ❌ | 5.9.10+ |
| argo-common-workflows | upload-model-to-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
| async-parsing | async-parsing | tika-server | ✅ | ✅ | 5.9.9+ |
| async-parsing | async-parsing | async-parsing | ✅ | ✅ | 5.9.9+ |
| auth-ui | auth-ui | auth-ui | ✅ | ✅ | 5.9.9+ |
| classic-rest-service | classic-rest-service | init/import-certs | ✅ | ✅ | 5.9.10+ |
| classic-rest-service | classic-rest-service | classic-rest-service | ✅ | ✅ | 5.9.9+ |
| classification | argo/classification | init/wait/main | ✅ | ❌ | 5.9.10+ |
| connector-plugin | connector-plugin | init/import-certs | ✅ | ❌ | 5.9.10+ |
| connector-plugin | connector-plugin | connector-plugin | ✅ | ✅ | 5.9.9+ |
| connectors | connectors | connectors | ✅ | ✅ | 5.9.9+ |
| connectors-backend | CRD | ✅ | ✅ | 5.9.9+ | |
| connectors-backend | connectors-backend | connectors-backend | ✅ | ✅ | 5.9.9+ |
| fusion-admin | fusion-admin | admin | ✅ | ✅ | 5.9.9+ |
| fusion-commons | check-admin | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-api-gateway | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-indexing | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-kafka | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-logstash | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-pulsar | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | setup-keystore-and-properties | ✅ | ✅ | 5.9.9+ | |
| fusion-commons | check-zk | ✅ | ✅ | 5.9.9+ | |
| fusion-config-sync | fusion-config-sync | fusion-config-sync | ✅ | ✅ | 5.9.9+ |
| fusion-data-augmentation | argo/data-augmentation/volume-fix | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/init-workspace | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/write-job-configs | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/write-io-configs | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/add-zkhost | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/pull-data-training-and-metadata | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/pull-data-training-and-metadata-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/volume-fix2 | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/synonym-list | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/download-synonym-dictionary | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/keystroke-list | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/download-keystroke-blob | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/augment | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/push-augmented-data | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-data-augmentation | argo/data-augmentation/push-augmented-data-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
| fusion-indexing | fusion-indexing | fusion-indexing | ✅ | ✅ | 5.9.9+ |
| fusion-resources | fusion-resources-secret-hook | setup-keystore-and-properties | ✅ | ✅ | 5.9.10+ |
| insights | insights | insights | ✅ | ✅ | 5.9.9+ |
| job-launcher | job-launcher | job-launcher | ✅ | ✅ | 5.9.9+ |
| job-launcher | job-launcher | kubectl-runner | ✅ | ✅ | 5.9.9+ |
| job-launcher | job-launcher-spark-cleanup | kubectl-runner | ✅ | ✅ | 5.9.9+ |
| job-launcher | spark-kubernetes-driver | spark-kubernetes-driver | ✅ | ❌ | 5.9.10+ |
| job-launcher | spark-kubernetes-executor | spark-kubernetes-executor | ✅ | ❌ | 5.9.10+ |
| job-rest-server | job-rest-server | job-rest-server | ✅ | ✅ | 5.9.9+ |
| kafka | kafka-metrics | kafka-exporter-archived | ✅ | ❌ | 5.9.10+ |
| kafka | kafka-provisioning | init/wait-for-available-kafka | ✅ | ❌ | 5.9.10+ |
| kafka | kafka-provisioning | kafka-provisioning | ✅ | ❌ | 5.9.10+ |
| kafka | kafka | kafka | ✅ | ❌ | 5.9.10+ |
| kafka | kafka | jmx-exporter | ✅ | ❌ | 5.9.10+ |
| kafka | kafka | init/check-zk | ✅ | ✅ | 5.9.9+ |
| kafka | kafka | init/auto-discovery | ✅ | ❌ | 5.9.10+ |
| kafka | kafka | init/volume-permissions | ✅ | ❌ | 5.9.10+ |
| lwai-gateway | lwai-gateway | lwai-gateway | ✅ | ✅ | 5.9.9+ |
| ml-model-service | ml-model-service | java-service | ✅ | ✅ | 5.9.9+ |
| ml-model-service | ml-model-service-namespace-hook | kubectl-runner | ✅ | ✅ | 5.9.9+ |
| ml-model-service/ambassador | ambassador | ambassador | ✅ | ❌ | 5.9.10+ |
| ml-model-service/ambassador | ambassador | prometheus-exporter | ✅ | ❌ | 5.9.10+ |
| ml-model-service/milvus | milvus-writable | milvus | ✅ | ❌ | 5.9.10+ |
| ml-model-service/milvus | milvus-writable | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
| ml-model-service/milvus | milvus-writable | init/create-for-share-storage | ✅ | ❌ | 5.9.10+ |
| ml-model-service/milvus | milvus-admin | admin | ✅ | ❌ | 5.9.10+ |
| ml-model-service/milvus | milvus-admin | init/wait-for-milvus | ✅ | ✅ | 5.9.10+ |
| ml-model-service/milvus | milvus-mishards | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
| ml-model-service/milvus | milvus-mishards | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
| ml-model-service/milvus | milvus-mishards | mishards | ✅ | ❌ | 5.9.10+ |
| ml-model-service/milvus/mysql | mysql | init/remove-lost-found | ✅ | ✅ | 5.9.10+ |
| ml-model-service/milvus/mysql | mysql | mysql | ✅ | ❌ | 5.9.10+ |
| pm-ui | pm-ui | pm-ui | ✅ | ✅ | 5.9.9+ |
| query-pipeline | query-pipeline | query-pipeline | ✅ | ✅ | 5.9.9+ |
| question-answering | argo/qna-coldstart/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/add-zkHost | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/pull-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/pull-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/post-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-coldstart/apply-seldon-deployment | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/pull-qa-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/pull-qa-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/train-with-texts | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/post-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-supervised/apply-seldon-deployment | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/pull-eval-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/pull-eval-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/evaluate | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/push-eval-results-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| question-answering | argo/qna-evaluation/push-eval-results | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/pull-data-training-and-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/pull-data-training-and-metadata-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/train-with-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/train-without-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/push-recommendations | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/push-recommendations-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/add-default-exclude-query | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-user/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/copy-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/pull-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/pull-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/push-content | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/push-content-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/add-default-exclude-query | init/wait/main | ✅ | ❌ | 5.9.10+ |
| recommender | argo/item-recommender-content/delete-old-content-recommendations | init/wait/main | ✅ | ❌ | 5.9.10+ |
| reverse-search | reverse-search | init/set-reverse-search-zone | ✅ | ✅ | 5.9.10+ |
| reverse-search | reverse-search | init/check-zk | ✅ | ✅ | 5.9.9+ |
| reverse-search | reverse-search | init/enable-tls-in-reverse-search | ✅ | ✅ | 5.9.10+ |
| reverse-search | reverse-search | reverse-search | ✅ | ❌ | 5.9.10+ |
| rules-ui | rules-ui | rules-ui | ✅ | ✅ | 5.9.9+ |
| seldon-core-operator | seldon-controller-manager | manager | ✅ | ❌ | 5.9.10+ |
| seldon-core-operator | seldon-spartakus-volunteer | seldon-spartakus-volunteer | ✅ | ❌ | 5.9.9+ |
| seldon-core-operator | crd/SeldonDeployment | ✅/❌ | ❌ | 5.9.9+ | |
| solr | solr | init/set-solr-zone | ✅ | ✅ | 5.9.10+ |
| solr | solr | init/enable-tls-in-solr | ✅ | ✅ | 5.9.10+ |
| solr | configset-bootstrap | configset-bootstrap | ✅ | ✅ | 5.9.10+ |
| solr | solr | solr | ✅ | ❌ | 5.9.10+ |
| solr | solr-exporter | exporter | ✅ | ❌ | 5.9.10+ |
| solr | solr-exporter | init/solr-init | ✅ | ✅ | 5.9.10+ |
| solr-managed | configset-bootstrap | configset-bootstrap | ✅ | ✅ | 5.9.10+ |
| solr-managed | exporter | exporter | ✅ | ❌ | 5.9.10+ |
| solr-managed | exporter | init/solr-init | ✅ | ✅ | 5.9.10+ |
| solr-managed | solr | init/set-solr-zone | ✅ | ✅ | 5.9.10+ |
| solr-managed | solr | init/enable-tls-in-solr | ✅ | ✅ | 5.9.10+ |
| solr-managed | solr | solr | ✅ | ❌ | 5.9.10+ |
| solr-managed | solr | process-raw | ✅ | ❌ | 5.9.10+ |
| solr-backup-runner | solr-backup-runner-backup | solr-backups | ✅ | ❌ | 5.9.10+ |
| solr-backup-runner | solr-backup-runner-prune | solr-prune | ✅ | ❌ | 5.9.10+ |
| templating | templating | templating | ✅ | ✅ | 5.9.9+ |
| webapps | webapps | webapps | ✅ | ✅ | 5.9.9+ |
| zookeeper | zookeeper | zookeeper | ✅ | ❌ | 5.9.10+ |
| zookeeper | zookeeper | jmx-exporter | ✅ | ❌ | 5.9.10+ |
| zookeeper | zookeeper | zookeeper-exporter | ✅ | ❌ | 5.9.10+ |
| zookeeper | zookeeper-chroots | main | ✅ | ❌ | 5.9.10+ |
| Chart Name | Pod Name | Container Name | Supported | Default enabled | Supported version |
|---|---|---|---|---|---|
admin-ui | admin-ui | admin-ui | ✅ | ✅ | 5.9.9+ |
api-gateway | api-gateway | init/api-gateway | ✅ | ✅ | 5.9.9+ |
api-gateway | api-gateway | api-gateway | ✅ | ✅ | 5.9.9+ |
api-gateway | api-gateway | generate-jks | ✅ | ✅ | 5.9.9+ |
apps-manager | apps-manager | apps-manager | ✅ | ✅ | 5.9.9+ |
argo | argo-server | argo-server | ✅ | ❌ | 5.9.10+ |
argo | argo-executor | executor | ✅ | ❌ | 5.9.10+ |
argo | argo-mainContainer | mainContainer | ✅ | ❌ | 5.9.10+ |
argo | argo-controller | controller | ✅ | ✅ | 5.9.10+ |
argo/minio | minio | minio | ✅ | ❌ | 5.9.10+ |
argo/minio | minio | minio | ✅ | ❌ | 5.9.10+ |
argo/minio | make-bucket-job | minio-mc | ✅ | ❌ | 5.9.10+ |
argo-common-workflows | delete-model | init/main/wait | ✅ | ❌ | 5.9.10+ |
argo-common-workflows | deploy-model | init/main/wait | ✅ | ❌ | 5.9.10+ |
argo-common-workflows | milvus-maintenance | init/main/wait | ✅ | ❌ | 5.9.10+ |
argo-common-workflows | upload-model-to-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
async-parsing | async-parsing | tika-server | ✅ | ✅ | 5.9.9+ |
async-parsing | async-parsing | async-parsing | ✅ | ✅ | 5.9.9+ |
auth-ui | auth-ui | auth-ui | ✅ | ✅ | 5.9.9+ |
classic-rest-service | classic-rest-service | init/import-certs | ✅ | ✅ | 5.9.10+ |
classic-rest-service | classic-rest-service | classic-rest-service | ✅ | ✅ | 5.9.9+ |
classification | argo/classification | init/wait/main | ✅ | ❌ | 5.9.10+ |
connector-plugin | connector-plugin | init/import-certs | ✅ | ❌ | 5.9.10+ |
connector-plugin | connector-plugin | connector-plugin | ✅ | ✅ | 5.9.9+ |
connectors | connectors | connectors | ✅ | ✅ | 5.9.9+ |
connectors-backend | CRD | ✅ | ✅ | 5.9.9+ | |
connectors-backend | connectors-backend | connectors-backend | ✅ | ✅ | 5.9.9+ |
fusion-admin | fusion-admin | admin | ✅ | ✅ | 5.9.9+ |
fusion-commons | check-admin | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-api-gateway | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-indexing | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-kafka | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-logstash | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-pulsar | ✅ | ✅ | 5.9.9+ | |
fusion-commons | setup-keystore-and-properties | ✅ | ✅ | 5.9.9+ | |
fusion-commons | check-zk | ✅ | ✅ | 5.9.9+ | |
fusion-config-sync | fusion-config-sync | fusion-config-sync | ✅ | ✅ | 5.9.9+ |
fusion-data-augmentation | argo/data-augmentation/volume-fix | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/init-workspace | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/write-job-configs | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/write-io-configs | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/add-zkhost | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/pull-data-training-and-metadata | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/pull-data-training-and-metadata-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/volume-fix2 | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/synonym-list | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/download-synonym-dictionary | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/keystroke-list | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/download-keystroke-blob | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/augment | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/push-augmented-data | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-data-augmentation | argo/data-augmentation/push-augmented-data-cloud | init/main/wait | ✅ | ❌ | 5.9.10+ |
fusion-indexing | fusion-indexing | fusion-indexing | ✅ | ✅ | 5.9.9+ |
fusion-resources | fusion-resources-secret-hook | setup-keystore-and-properties | ✅ | ✅ | 5.9.10+ |
insights | insights | insights | ✅ | ✅ | 5.9.9+ |
job-launcher | job-launcher | job-launcher | ✅ | ✅ | 5.9.9+ |
job-launcher | job-launcher | kubectl-runner | ✅ | ✅ | 5.9.9+ |
job-launcher | job-launcher-spark-cleanup | kubectl-runner | ✅ | ✅ | 5.9.9+ |
job-launcher | spark-kubernetes-driver | spark-kubernetes-driver | ✅ | ❌ | 5.9.10+ |
job-launcher | spark-kubernetes-executor | spark-kubernetes-executor | ✅ | ❌ | 5.9.10+ |
job-rest-server | job-rest-server | job-rest-server | ✅ | ✅ | 5.9.9+ |
kafka | kafka-metrics | kafka-exporter-archived | ✅ | ❌ | 5.9.10+ |
kafka | kafka-provisioning | init/wait-for-available-kafka | ✅ | ❌ | 5.9.10+ |
kafka | kafka-provisioning | kafka-provisioning | ✅ | ❌ | 5.9.10+ |
kafka | kafka | kafka | ✅ | ❌ | 5.9.10+ |
kafka | kafka | jmx-exporter | ✅ | ❌ | 5.9.10+ |
kafka | kafka | init/check-zk | ✅ | ✅ | 5.9.9+ |
kafka | kafka | init/auto-discovery | ✅ | ❌ | 5.9.10+ |
kafka | kafka | init/volume-permissions | ✅ | ❌ | 5.9.10+ |
lwai-gateway | lwai-gateway | lwai-gateway | ✅ | ✅ | 5.9.9+ |
ml-model-service | ml-model-service | java-service | ✅ | ✅ | 5.9.9+ |
ml-model-service | ml-model-service-namespace-hook | kubectl-runner | ✅ | ✅ | 5.9.9+ |
ml-model-service/ambassador | ambassador | ambassador | ✅ | ❌ | 5.9.10+ |
ml-model-service/ambassador | ambassador | prometheus-exporter | ✅ | ❌ | 5.9.10+ |
ml-model-service/milvus | milvus-writable | milvus | ✅ | ❌ | 5.9.10+ |
ml-model-service/milvus | milvus-writable | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
ml-model-service/milvus | milvus-writable | init/create-for-share-storage | ✅ | ❌ | 5.9.10+ |
ml-model-service/milvus | milvus-admin | admin | ✅ | ❌ | 5.9.10+ |
ml-model-service/milvus | milvus-admin | init/wait-for-milvus | ✅ | ✅ | 5.9.10+ |
ml-model-service/milvus | milvus-mishards | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
ml-model-service/milvus | milvus-mishards | init/wait-for-mysql | ✅ | ✅ | 5.9.10+ |
ml-model-service/milvus | milvus-mishards | mishards | ✅ | ❌ | 5.9.10+ |
ml-model-service/milvus/mysql | mysql | init/remove-lost-found | ✅ | ✅ | 5.9.10+ |
ml-model-service/milvus/mysql | mysql | mysql | ✅ | ❌ | 5.9.10+ |
pm-ui | pm-ui | pm-ui | ✅ | ✅ | 5.9.9+ |
query-pipeline | query-pipeline | query-pipeline | ✅ | ✅ | 5.9.9+ |
question-answering | argo/qna-coldstart/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/add-zkHost | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/pull-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/pull-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/post-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-coldstart/apply-seldon-deployment | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/pull-qa-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/pull-qa-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/train-with-texts | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/post-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-supervised/apply-seldon-deployment | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/list-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/pull-eval-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/pull-eval-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/evaluate | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/push-eval-results-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
question-answering | argo/qna-evaluation/push-eval-results | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/pull-data-training-and-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/pull-data-training-and-metadata-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/train-with-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/train-without-metadata | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/push-recommendations | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/push-recommendations-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/add-default-exclude-query | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-user/init-workspace | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/copy-model | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/write-job-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/write-io-configs | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/add-zkhost | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/pull-data | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/pull-data-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/train | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/push-content | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/push-content-cloud | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/add-default-exclude-query | init/wait/main | ✅ | ❌ | 5.9.10+ |
recommender | argo/item-recommender-content/delete-old-content-recommendations | init/wait/main | ✅ | ❌ | 5.9.10+ |
reverse-search | reverse-search | init/set-reverse-search-zone | ✅ | ✅ | 5.9.10+ |
reverse-search | reverse-search | init/check-zk | ✅ | ✅ | 5.9.9+ |
reverse-search | reverse-search | init/enable-tls-in-reverse-search | ✅ | ✅ | 5.9.10+ |
reverse-search | reverse-search | reverse-search | ✅ | ❌ | 5.9.10+ |
rules-ui | rules-ui | rules-ui | ✅ | ✅ | 5.9.9+ |
seldon-core-operator | seldon-controller-manager | manager | ✅ | ❌ | 5.9.10+ |
seldon-core-operator | seldon-spartakus-volunteer | seldon-spartakus-volunteer | ✅ | ❌ | 5.9.9+ |
seldon-core-operator | crd/SeldonDeployment | ✅/❌ | ❌ | 5.9.9+ | |
solr | solr | init/set-solr-zone | ✅ | ✅ | 5.9.10+ |
solr | solr | init/enable-tls-in-solr | ✅ | ✅ | 5.9.10+ |
solr | configset-bootstrap | configset-bootstrap | ✅ | ✅ | 5.9.10+ |
solr | solr | solr | ✅ | ❌ | 5.9.10+ |
solr | solr-exporter | exporter | ✅ | ❌ | 5.9.10+ |
solr | solr-exporter | init/solr-init | ✅ | ✅ | 5.9.10+ |
solr-managed | configset-bootstrap | configset-bootstrap | ✅ | ✅ | 5.9.10+ |
solr-managed | exporter | exporter | ✅ | ❌ | 5.9.10+ |
solr-managed | exporter | init/solr-init | ✅ | ✅ | 5.9.10+ |
solr-managed | solr | init/set-solr-zone | ✅ | ✅ | 5.9.10+ |
solr-managed | solr | init/enable-tls-in-solr | ✅ | ✅ | 5.9.10+ |
solr-managed | solr | solr | ✅ | ❌ | 5.9.10+ |
solr-managed | solr | process-raw | ✅ | ❌ | 5.9.10+ |
solr-backup-runner | solr-backup-runner-backup | solr-backups | ✅ | ❌ | 5.9.10+ |
solr-backup-runner | solr-backup-runner-prune | solr-prune | ✅ | ❌ | 5.9.10+ |
templating | templating | templating | ✅ | ✅ | 5.9.9+ |
webapps | webapps | webapps | ✅ | ✅ | 5.9.9+ |
zookeeper | zookeeper | zookeeper | ✅ | ❌ | 5.9.10+ |
zookeeper | zookeeper | jmx-exporter | ✅ | ❌ | 5.9.10+ |
zookeeper | zookeeper | zookeeper-exporter | ✅ | ❌ | 5.9.10+ |
zookeeper | zookeeper-chroots | main | ✅ | ❌ | 5.9.10+ |
Restrictive mode for query pipelines
In Fusion 5.9.15 and later, you can choose restrictive mode for any query pipeline. Restrictive mode safeguards the pipeline against unintended or unsafe changes. The default mode is permissive mode. See Restrictive Mode for complete details about how restrictive mode works and how to enable it.Lucidworks AI Gateway
Lucidworks AI Gateway acts as a bridge between Fusion and Lucidworks AI, handling the complexities of authentication and communication. By managing credentials and other sensitive information behind the scenes, it ensures that Fusion can interact with Lucidworks AI without exposing the details of the underlying accounts or requiring manual authentication. In Lucidworks AI, you have one or more integrations that each represent a set of credentials and a security scope. When you add an integration to Lucidworks AI Gateway, it allows Fusion to seamlessly connect to Lucidworks AI at any time without additional authentication. The diagram below displays the interaction between Lucidworks AI and Fusion. Note that Lucidworks AI Gateway only posts to Lucidworks AI; Lucidworks Platform and Lucidworks AI cannot reach out to Lucidworks AI Gateway or to Fusion.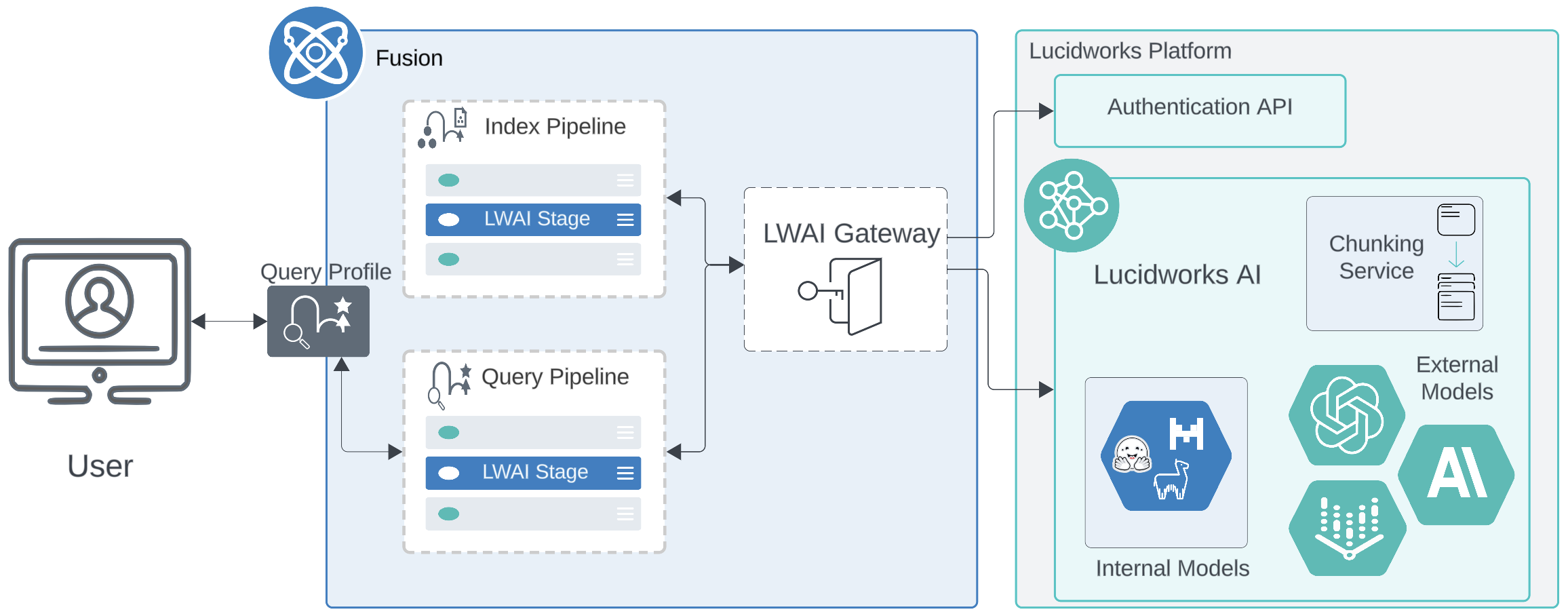
Fusion firewall and port considerations
Lucidworks AI Gateway is a critical component of Lucidworks Fusion, enabling secure and authenticated communication between Fusion and Lucidworks AI. It facilitates seamless integration with AI-powered search enhancements by managing credentials and access permissions. To function correctly, thelwai-gateway pod must be able to communicate externally on port 443 for:
- Authentication service: Okta authentication hosted at identity.lucidworks.com for secure OAuth-based authentication.
- LWAI services: Reaching the private LWAI endpoint hosted on the Lucidworks Platform.
Security and configuration
Lucidworks AI Gateway securely handles API credentials and account scopes, allowing Fusion to interact with AI models without exposing sensitive data. Configuration is managed using Helm values files, ensuring flexible multi-integration support for Fusion instances. By ensuring proper firewall rules and secure credentials management, the Lucidworks AI Gateway enables a robust AI-powered search experience within Fusion.Learn more
Configure Active Directory Federation Services (AD FS) authentication for Fusion
Configure Active Directory Federation Services (AD FS) authentication for Fusion
You can configure Active Directory Federation Services (AD FS) for SAML single sign-on (SSO) authentication in Fusion. This guide explains how to set up Spring Boot OAuth2 with AD FS.Replace the
OAuth-based authentication against AD FS requires AD FS 3.0 or later which is available from Windows Server 2012 R2 onwards.
Configure a Security Realm in Fusion
In Fusion, create a Security Realm for AD FS.- In the Fusion workspace, navigate to System > Access Control.
- Click Security Realms.
- Click Add Security Realm.
-
Enter the following information for the new realm:
- Enter a Name. The name must be unique and should be descriptive yet short.
- Select saml from the Type pulldown menu.
- The default value for Enabled is true. This setting controls whether or not Fusion allows user logins for this security realm.
- The default value for Ephemeral Users is false. When disabled, this setting prevents ephemeral users from being created in ZooKeeper during login. If enabled, this property negates Auto Create Users.
- The default value for Auto Create Users is true. If enabled, a user account is created automatically upon initial authentication. If disabled, then a Fusion user with admin permissions must create Fusion users.
-
Enter the Identity Provider URL. This URL is used by the SAML authority for single sign-on. For example:
https://www.example.com/APP-PATH/adfs/ls -
Enter the URL of the IdP Issuer. For example:
http://www.example.com/adfs/services/trust.- IdP Issuer must match
<saml:Issuer>in the SAML payload.
- IdP Issuer must match
-
Optional: Provide the App Issuer. This field is required if there is an
audienceRestrictionin the SAML assertion and must match<saml:Audience>in the SAML payload. - In the Certificate Fingerprint, paste the contents of the SAML authority certificate, without the certificate header and footer.
- Optional: Enter the User ID Attribute. By default, the Fusion username is the same as the login name known to the Identity Provider. When another field or attribute in the user record stored by the IdP should be used as the Fusion username, that attribute name is the value of the User ID Attribute.
- Optional: Provide a Post Login Redirect URL. If not set, the Fusion URL is used.
-
Optional: Provide a Logout URL.
- Optional: Under Groups Mapping, specify the Group Name Attribute and add group mappings.
- Click Save.
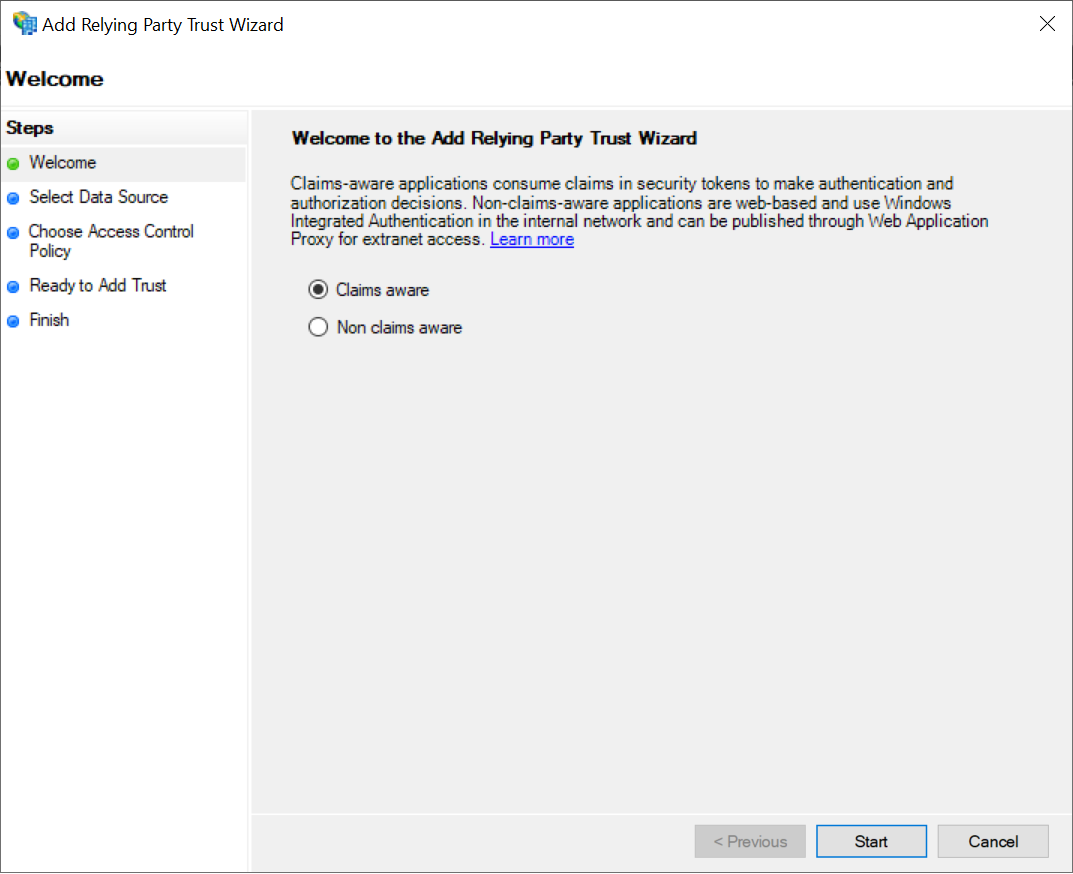
Set up the application (relying party trust) in AD FS
Create a relying party trust in the AD FS Management console. For more details, refer to the Microsoft AD FS documentation.The following screenshots may differ from your setup depending on the version of AD FS you’re using.
-
Launch the Add Relying Party Trust Wizard, then select Claims aware.
-
Choose the option to enter the data manually.
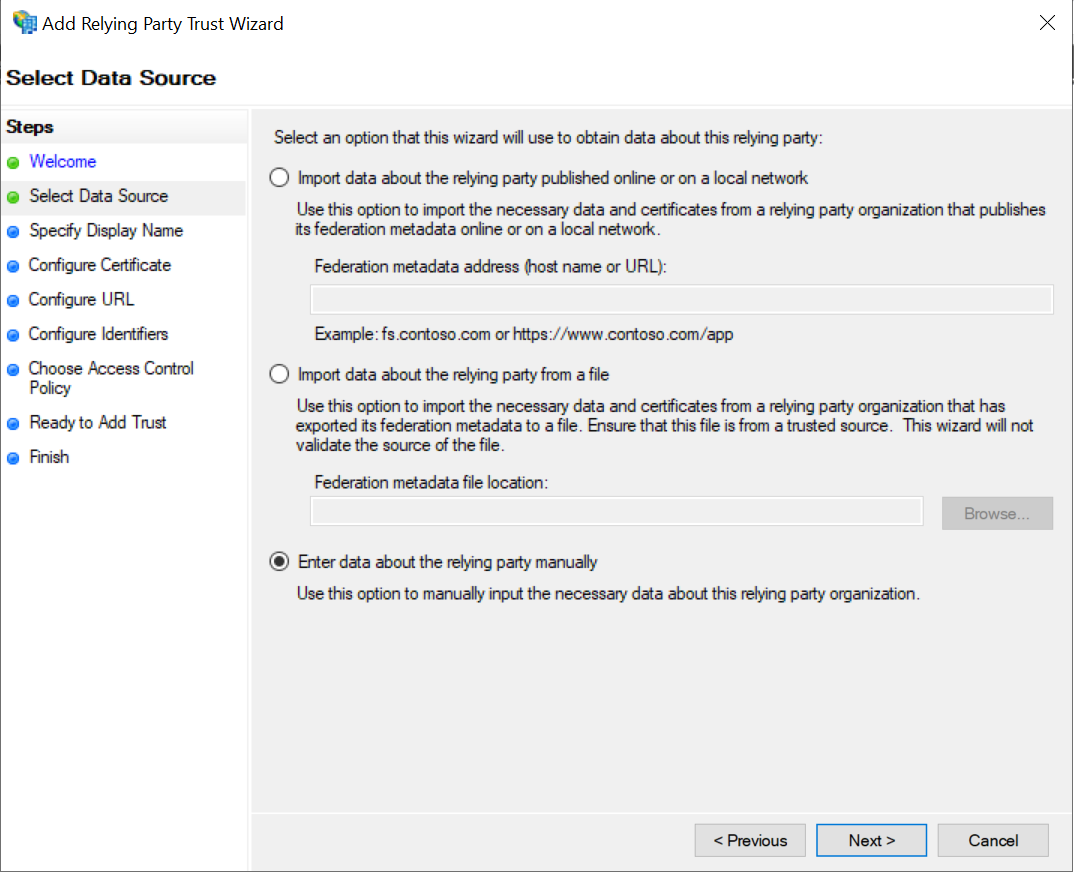
-
Set a Display name.
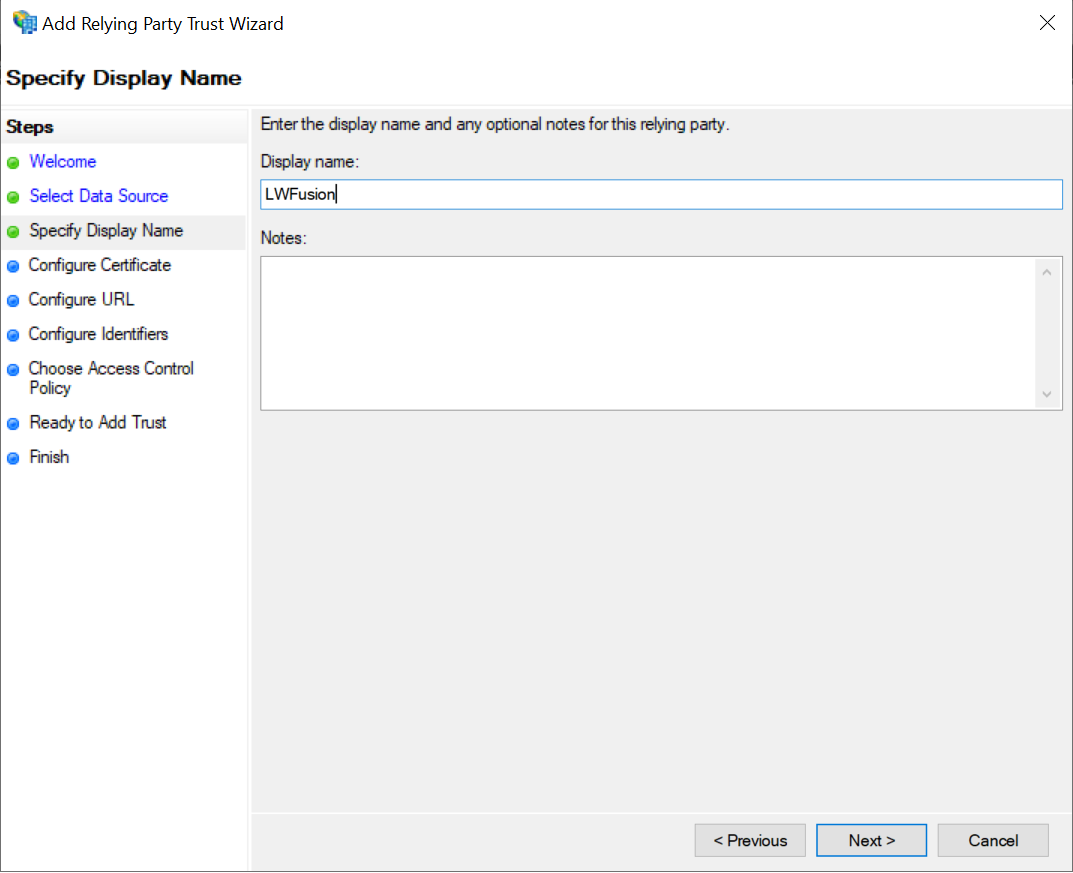
-
Configure URL. Enable the option for SAML 2.0 WebSSO protocol.
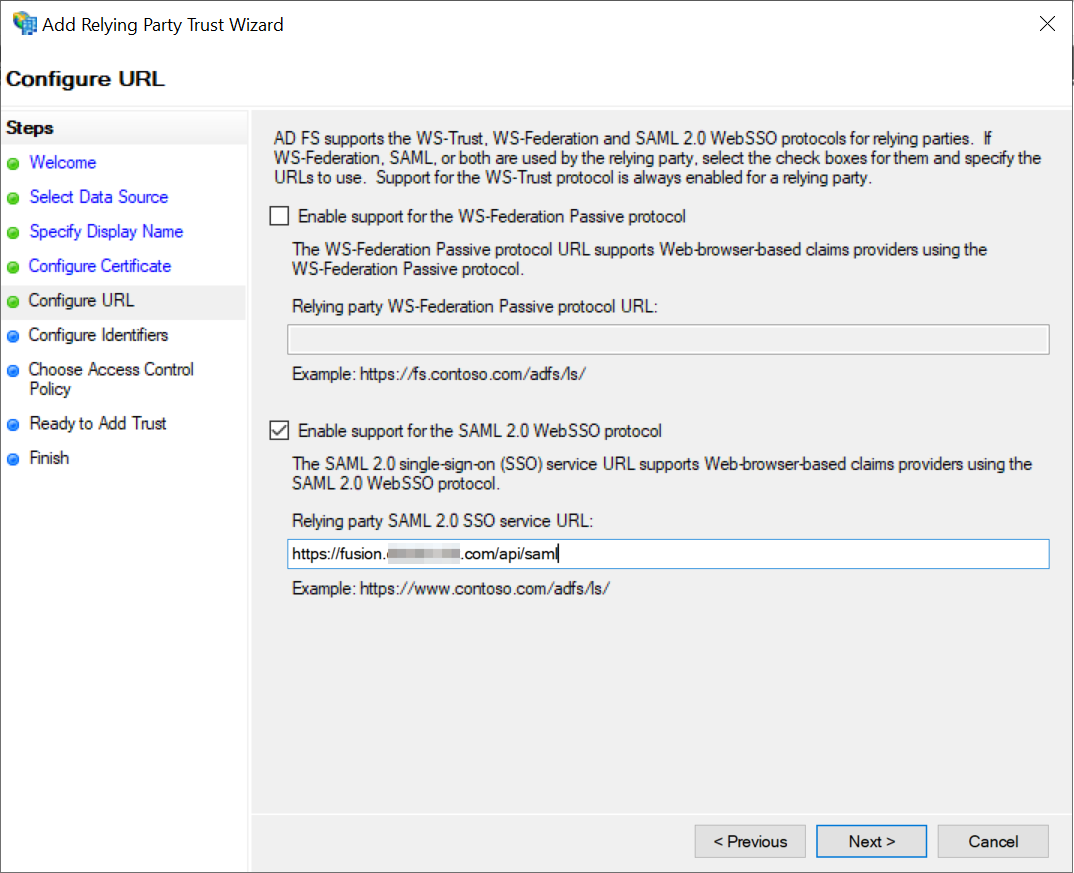
-
Set the Relying party trust identifier to the URL of the Fusion application.
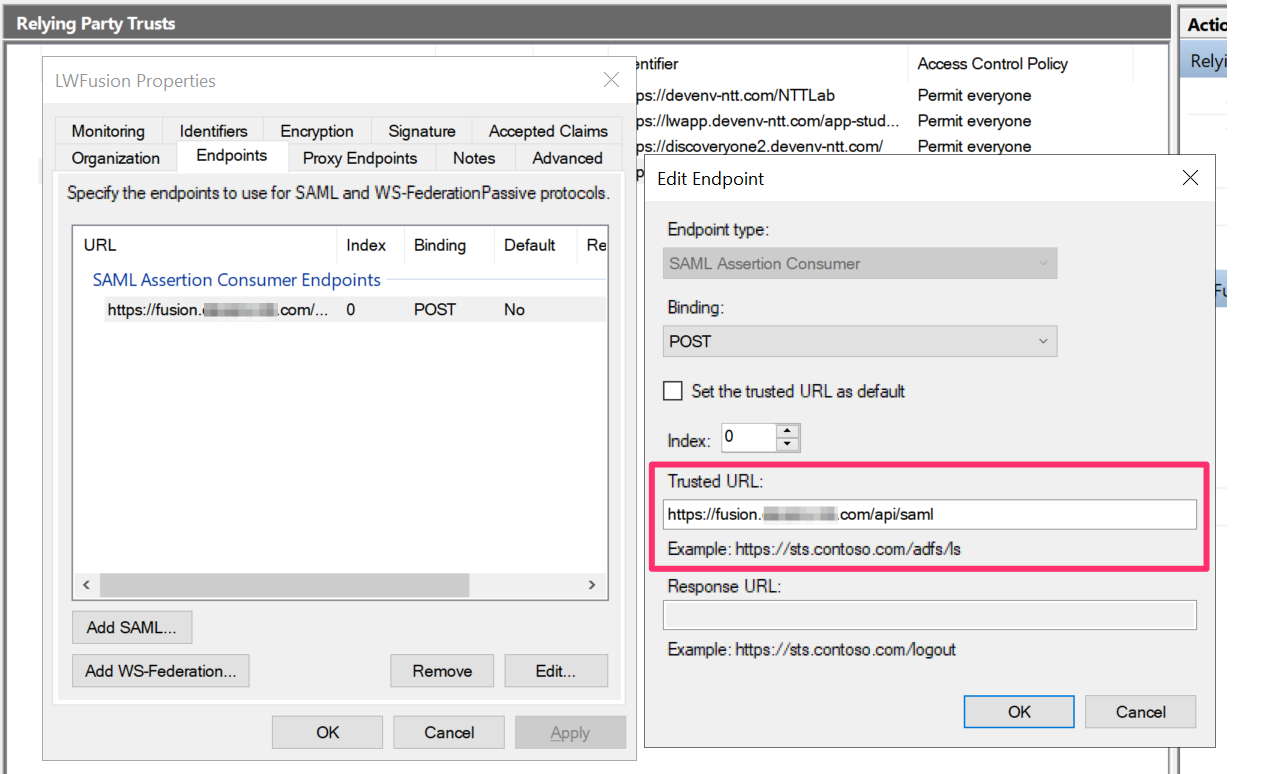
-
Edit the Claim Rules to pass through the User Principal Name as the
NameIDclaim.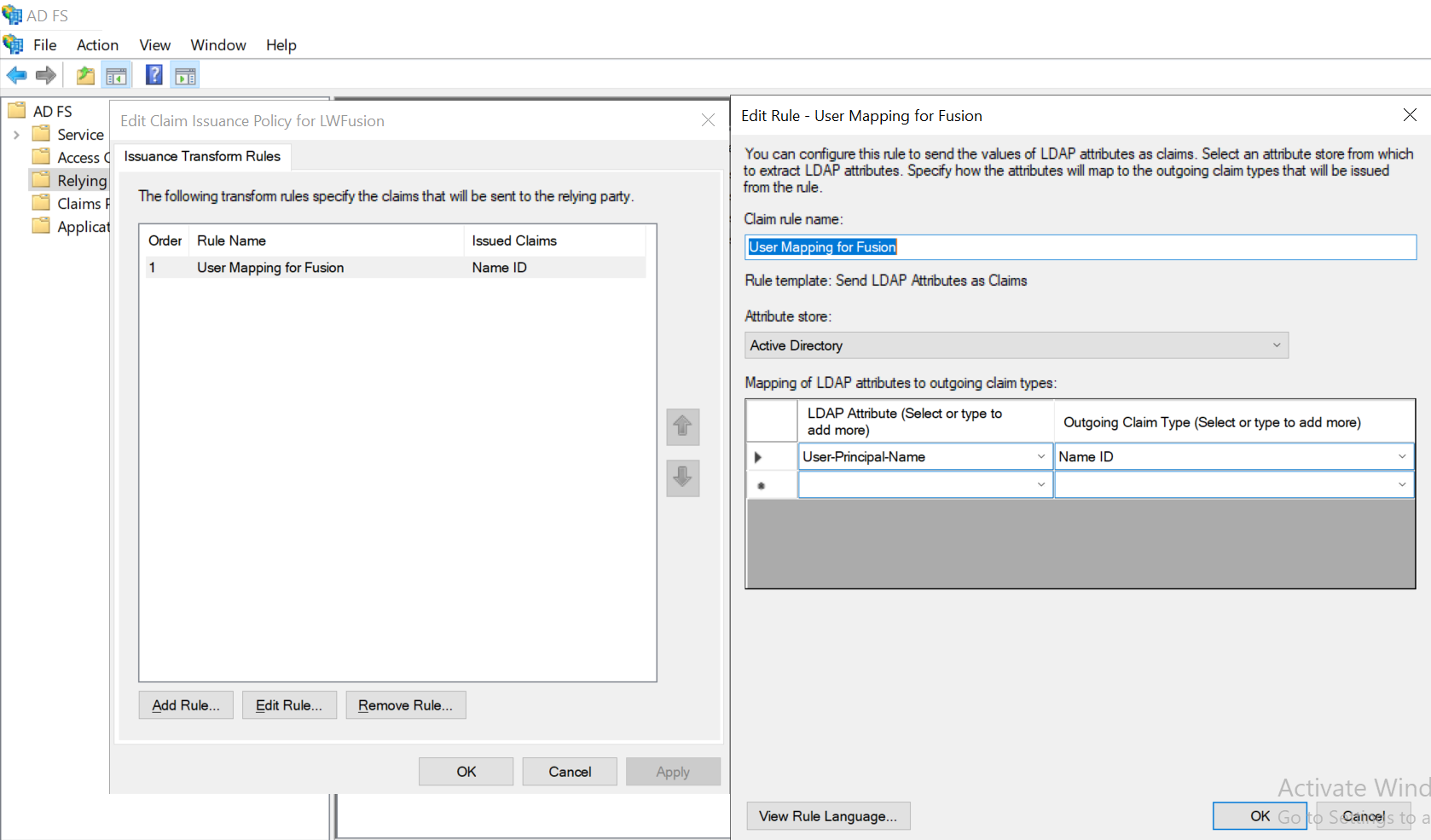
-
In a terminal, create the OAuth AD FS
clientfor the Fusion application:
ClientId should be a GUID and the RedirectUri must point to the Fusion application URL, with /oauthLogin appended. Here, localhost is used for testing a Fusion application running on the local development machine.Configure the OAuth module for the application setup in AD FS
Create a new configuration file inconf/security/oauth.conf.client-id, adfs-url and resource parameters for your environment.- The
client-idis the ID that was set up against AD FS using theAdd-ADFSClientPowerShell command. - The
adfs-urlis the URL of the AD FS server with the/adfscontext appended. - The
resourceis the relying party trust identifier set up in AD FS management. - The
high-trustparameter is only required when integrating the AD FS and SharePoint modules. This article is only concerned with authentication against AD FS.
Test the authentication
When a user goes to the Fusion login page, they will be redirected to the AD FS OAuth login page. After the user logs in, the user will be returned to Fusion as an authenticated user. The Fusion user’s details will also be populated with any basic information available from the decoded OAuth token such as roles and the user principal name.Create a Java Keystore for Use with Fusion
Create a Java Keystore for Use with Fusion
Enterprise customers may want to use a signed certificate from an Enterprise Certificate Authority (CA), such as GoDaddy or Let’s Encrypt for their Fusion 5 deployment.The Fusion 5 default setup will create a self-signed Java Keystore (JKS) file that is used as the JSON Web Token (JWT) signer.The following instructions detail how to create the 4. Import the signed certificate into the
5. Upload the
The api-gateway service will pull down the
api-gateway.jks file using a CA signed certificate.Prerequisites
New installations
1. Create a JKS
Run the following command, replacing thedname(Distinguished Name) field with the name that matches your customer environment, and the keypass and storepass fields with a secure password.This will create the api-gateway.jks:keytool -genkeypair -keyalg rsa -keysize 2048 -validity 3650 -dname "CN=sample, OU=sample, O=sample, L=sample, S=sample, C=sample" -storetype jks -keystore api-gateway.jks -keypass password -storepass password -alias jwt-signer2. Create a Certificate Signing Request (CSR)
Run the following command to create a newfusion.csr, which will be sent to the CA:keytool -keystore api-gateway.jks -certreq -alias jwt-signer -file fusion.csr3. Send the CSR to your CA to get a signed certificate
The CA will return one of two possible responses:-
A PKCS12 certificate file, such as
CAreply.pkcs. This is a full keystore containing all the keys you need, including the root certificate and the signed chain certificate. -
Several PEM files, such as
0000_cert.pem,0000_chain.pem, and0001_chain.pem. These files contain the root certificate, the chain certificate(s), and the signed chain certificate.
4. Import the signed certificate into the api-gateway.jks
- If you received a PKCS file, import it using the following keytool command:
keytool -importcert -alias jwt-signer -file <CAreply.pkcs> -keystore api-gateway.jks -trustcacerts- If you receive PEM files, run the following commands to import the keys:
keytool -importcert -alias root -file 0000_cert.pem -keystore api-gateway.jks -trustcacertskeytool -importcert -alias intermediate -file 0000_chain.pem -keystore api-gateway.jks -trustcacertskeytool -importcert -alias jwt-signer -file 0001_chain.pem -keystore api-gateway.jks -trustcacerts
5. Upload the api-gateway.jks as a Kubernetes generic secret
The api-gateway service will pull down the api-gateway.jks file during initialization as a Kubernetes secret:- Delete the
<namespace>-api-gateway.jkssecret if it already exists. - Upload the new secret with the following command:
k create secret generic <namespace>-api-gateway-jks --from-file api-gateway.jks6. Install Fusion 5 using Helm
See Deploy Fusion 5 on Other Kubernetes Platforms for more information.Existing installation
1. Create a JKS with your CA certificate or the java keytool
If you are using the Java keytool, you can run the same command used in the Create a JKS section:keytool -genkeypair -keyalg rsa -keysize 2048 -validity 3650 -dname "CN=sample, OU=sample, O=sample, L=sample, S=sample, C=sample" -storetype jks -keystore api-gateway.jks -keypass myPassword -storepass myPassword -alias jwt-signer2. Scale down Fusion deployment to 0
This step will allow Fusion services to find the latest JKS once it is scaled up at the final step.See Deploy Fusion at Scale for more information on the process.3. Delete the existing Kubernetes JKS secret for Fusion
As in the Upload theapi-gateway.jks as a Kubernetes generic secret section, delete the existing <namespace>-api-gateway.jks secret.4. Create a Kubernetes secret with the JKS using the name of the deployment
Upload a new secret using the api-gateway.jks file with the following command:k create secret generic <deployment>-api-gateway-jks --from-file api-gateway.jks5. Scale up Fusion deployment
Fusion should accept the JKS once this step is complete.Accessing HTTPS web resources with signed Enterprise/Self-signed CA Certificates
Accessing HTTPS web resources with signed Enterprise/Self-signed CA Certificates
Sometimes when you call out to HTTPS resources in connectors, index pipelines, query pipelines, or spark jobs, the HTTPS web resource is signed using an Enterprise or Self-Signed CA. This results in This creates Only use this option if you have installed Fusion using the
Caused by: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target.You can ignore all SSL validation, but that’s not secure.Whether it’s Spark, Connectors, Indexing, Query, or something else, adding trusted SSL certificates lets you can access these HTTPS web resources.Obtain each public certificate in .pem format.
The first thing you need is the public certificates in X.509 PEM format. Refer to How to save a remote server SSL certificate locally as a file for information on how to do this.One example is to run:/home/ndipiazza/Downloads/spark-ssl-test/badssl-com-chain.pem, which is a public certificate from a public self-signed HTTPS site.Trust store certificate option
- Embed at runtime each enterprise/self-signed certificate to a local trust store used by the Apache HttpClient.
Add each public certificate to the trust store
This option is only available in Fusion releases 5.9.2 and later.
$tlsEnabled=true, which follows this guide: Enable Transport Layer Security (TLS) for Fusion Microservices.The steps are to:- Download the truststore from the
fusion-truststoreKubernetes secret to a local folder. - Add any additional certificates to the truststore that you need using Java’s
keytool. - Upload the updated truststore back to the secrets store.
Verifying it works
Test access to this HTTPS resource with a Scala example. Below is an example Scala script that uses an Apache HttpClient that fetches a URL, but that URL is self-signed. If you you do not have this public certificate in your trust store, SSL validation will fail.In this example, we attempt to talk toself-signed.badssl.com, which is a public site with a self-signed SSL certificate. Prior to adding the SSL certificate into the trust store, it fails. When you add the cert, it works. Save this script as Collections → Job → Add → Script, then save this job and run it.Embed each enterprise/self-signed certificate to a local trust store used by the Apache HttpClient at runtime
This option embeds the public certificates for the trusted domains in the code, then inserts them into a local keystore used by Apache HttpClient.Use this approach:- If you do not have Kubernetes admin access to edit the keystore secret.
- If the HTTPS URL is isolated to a single job or pipeline stage, as it is simpler to do it this way versus adding it to the keystore.
How to use it
- Use the X.509 certificate file created earlier and copy it as text. In your program, create a map of
{alias, pem file string}calledtrustedPublicCertificatesthat contains your public certificates. - Replace
trustedPublicCertificateswith an alias name as the key of the map, then set the PEM file string contents as the value. - Use the Apache HttpClient to access the resource.